Identity theft is a crime in which a thief steals personal information to sell or to use for their own benefit. Once your information is in their hands, they can get a driver’s license, credit card and more…in your name! Any negative consequences due to their reckless behavior falls squarely on you and can damage your credit and your reputation. It is vital to take precautions to protect your identity. Here are 16 vital tips to help you prevent a bad guy from doing no good in your good name,
1. Identity Protection

Join an identity theft protection service. These companies offer ways to help you if you become victim to identity theft. Therefore, these services can’t prevent somebody from stealing your identity, but they can manage the damage after the fact, even if only slightly. For instance, if there is a security breach into an online web retailer’s client records which include your data, an identity protection program can monitor your personal information to see of it is being traded or sold as well as restore the integrity of your identity after a case of fraud. Monthly premiums can range from under $7.00 to under $15.00.
2. Use A Safe
![[#Beginning of Shooting Data Section] Nikon D2X 2009/08/14 17:21:59.2 JPEG (8-bit) Fine Image Size: Large (4288 x 2848) Color Lens: 24-70mm F/2.8 G Focal Length: 38mm Exposure Mode: Manual Metering Mode: Multi-Pattern 1/250 sec - F/16 Exposure Comp.: 0 EV Sensitivity: ISO 100 Optimize Image: White Balance: Preset d-2 AF Mode: Manual Flash Sync Mode: Flash Mode: Auto Flash Comp: Color Mode: Mode II (Adobe RGB) Tone Comp.: Normal Hue Adjustment: 0° Saturation: Normal Sharpening: Low Image Comment: Long Exposure NR: Off High ISO NR: Off [#End of Shooting Data Section]](http://www.lifed.com/wp-content/uploads/2016/10/21481-closed-in-floor-e1476428286243.jpg)
3. Protect Your Wallet

Protect your wallet and its contents. If keep your wallet on you, feel for it frequently (which you probably already do). If you carry it in a purse, make sure the purse has a zipper and zip it! Open bags are easy targets for slick pick pockets who leave their victims unaware. And never leave your wallet laying in plain sight in automobiles. Hide it under the seat or put it in the glove box. If you carry it with you, be aware of crowd hackers. These are computer-savvy pickpockets who can lift your credit card numbers as well as your identity just by walking near you. Devices like Signal Vault block their signal and protect your information. Check out Signal Vault here.
4. What’s In Your Wallet?

Know what’s in your wallet. Photocopy all of your credit cards, bank cards, identification cards and any personal information you have in your wallet. Keep the photocopies at home or someplace safe…but not in your wallet! If your wallet is missing, these photocopies will be very useful. They will allow you to read the phone numbers to your credit card companies and cancel the cards before a thief can purchase a flight to Honolulu. Copies will also let you know exactly what a thief took and what information he or she now has in their possession and allow you to freeze cards and order replacements quickly.
5. Check Monthly Statements
Check your monthly bank account statement carefully. This can take just a few minutes and save you many hours of heartache and many thousands of dollars in losses. Identify all the debits and payments to make sure somebody did not hack in and start paying themselves from your account. A small but unauthorized payment, withdraw or transfer each month can go unnoticed unless you employ a careful eye and go over each line of your statement. If you notice something suspicious, call your banking institution immediately.
6. Cancel Unused Credit Cards

Cancel unused credit cards. It’s easy to grow a pile of plastic by seizing on tempting introductory offers. But when the honeymoon period ends, that is, when you took advantage of the offer and then it’s over, what you’re left with is another card. While this may not be inherently bad, it just opens the door to potential problems. More cards also allows more opportunities for identity thieves to access your information. And that leads to more credit sources you have to monitor. Of course, cancelling a credit card will cause a little hit to your credit rating. So do not axe any cards soon before you plan to make a large purchase using credit.
7. Make Passwords Strong

Select passwords that are too difficult to be deciphered by cyber thieves and hack software. What separates your social security number, credit card numbers and security answers from deviant techies is a strong password. Some “don’ts” to avoid easily decodable passwords: DON’T reuse passwords or use the same password for multiple accounts. Avoid personal names and birth dates as well as keyboard patterns like QWERTY. A random mix of numbers, letters and symbols is good as well as random personal information from your distant past, like your first best friend’s name and maybe add symbols in the middle. To remember various passwords, keep a list of written hints, but not the actual passwords.
8. Clean Your Hard Drive

Erase hard drives before you sell or give away devices or computers. It’s important to do more than just delete your documents and information because deleted items can still be recovered. You have to wipe clean the memory. This will preserve your personal information and prevent it from landing in the wrong hands. First, restore your device to the factory settings. Find the instructions for this in the user’s manual or online. If you are still not sure how to do this, take it to a reliable retail outlet and ask them to help you. It will be worth the few dollars they charge, if they even charge. You can also get free scrubbing programs online which should make your gadget safe to give away.
9. Get Anti-Virus Anti-Spyware

Make sure you computer has anti-spyware and anti-virus software. You do not need to spend money to get good antivirus software for a personal computer that does not contain a ton of secret information. Paid programs offer added features you may not need. However, going the free route, you run the risk of selecting malware that’s disguised as anti-virus software. If you choose free, stick with a well-known product from a reputable company that you can test to check how well it performs. Spyware, on the other hand, is used to detect passwords, credit card numbers, surfing habits and more, including anything on your hard drive. Use extreme caution when downloading freeware from the Internet.
10. Don’t Give Out Info

Do not ever give your personal information over the phone, Internet, email, etc. to people with whom you are not familiar — or if they contact you. Sometimes, thieves will telephone you and speak very quickly to confuse you or claim to be from a vendor you use and request your personal information. Do not give it. If it’s a phone call, ask to call them back and get their phone number. Do not call back right away but later in the day when, if it’s a real company, somebody else is sure to answer and not expect your call. If it’s an email, check the email address carefully. If the name is spelled wrong or if it’s from a web-sourced email account like gmail or yahoo, these are red flags you are about to be scammed. (See #13.)
11. Monitor Your Credit

Monitor your credit. This is a sure way to uncover any wrongdoing, but it will do little to prevent fraud from happening in the first place. A credit reporting service will alert you to suspicious activity and this will shorten the time it would take you to detect any wrongdoing. This extra time will give you a slightly improved chance of minimizing any damage. The U.S. government Web site lets you obtain your credit report three times a year for free if you want to monitor it yourself. Just know that each time you check your credit score, it does not affect your credit. This is considered a “soft” inquiry. A lender or credit card issuer will conduct a “hard” inquiry and this will lower your score by a few points.
12. Shred, Shred, Shred

Do not put papers with personal information into the trash. Shred them first. Unfortunately, people walk around early the morning trash is collected and check for important documents or papers that have pertinent information. Others have been known to “dumpster dive” outside buildings to find pay dirt…which could be your financial information, passwords or personal information that can lead to clues about your passwords. Shredding financial statements as well as any documents with personal information is the safest way to protect you from somebody trying to obtain your identity.
13. Avoid Phishing
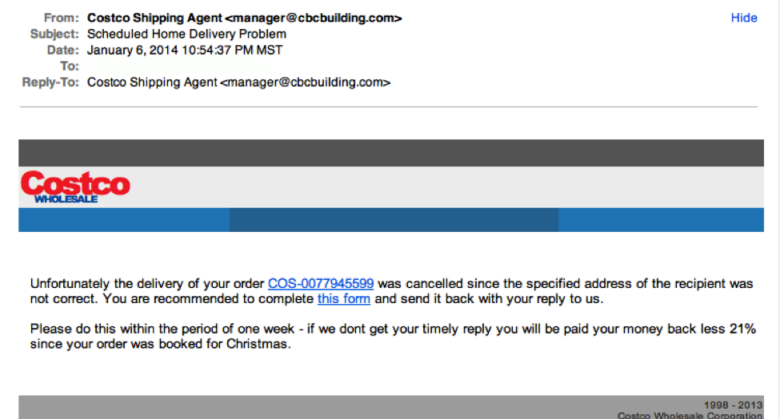
Don’t get phished. Phishing scams are emails supposedly sent to you from a business you use. In the email, they will ask you to verify security information or resubmit credit card information on a recent purchase. The email may even request account numbers or your login details. The email, sent from a deceptive address, may provide you with some of your own personal information to make you believe it is legitimately the company they are feigning to be. It might be your bank, your credit card company, your insurance agency or more. Never ever, ever, ever respond to any email with personal information, and do not click on links inside such an email. No trustworthy company will ever ask this of you via email.
14. Look For The Padlock

Be careful when shopping online. First, use a trusted online retailer, not whichever website shows up in a search. Next, before you give your credit card information, look for the lock. This symbol lets you know that the seller has SSL (secure sockets layer) encryption. The purchasing page will begin with HTTPS:// (notice the S) to show it’s secure. Then look for the icon of a locked padlock either in the address window next to the URL or in the status bar. This lets you know that the retailer uses a secured checkout to prevent your identity from being phished or swiped by a third party. Another precaution you can take is to dedicate a credit card for online purchases. This will help you monitor unauthorized purchases and freeze that card if necessary. Choose a card that provides online purchase and fraud protection.
15. Surf But Don’t Buy On Open WiFi

Don’t login to any website or use passwords on an open WiFi network. Using your smartphone in a store to comparison shop is smart. Browsing for a best seller while sitting in the park is safe, too. Making the purchase while you’re in a store or in the park, well, that’s not so smart. Public WiFi hotspots are especially vulnerable to hacking attacks. You would be better served waiting until you are on a secured network to click “Purchase,” like that which is probably in your home or business. It’s also a good idea to avoid purchasing or providing personal information on a public computer or device. It’s possible your information might be saved in the cache for the next user to access.
16. Use Your Passport

If you are flying on vacation or on business, use your passport in the security line as opposed to your driver’s license to prove your identity. The security personnel must check your identity against your airplane ticket, and most people show their driver’s license because it is usually readily accessible. But this could be a big problem if the security guard is dishonest. He or she can note your address, or photograph it, knowing you are away from home. This could lead to devastating results that you might not find out about until you return. Besides opening up your home to theft of property, the thief could take or copy documents with your personal information and account numbers you might not find out about for weeks or months.
[Featured Image Credit: www.noidentitytheft.com]
